Implementing Role-Based Access Control in a DOMAIN Environment
Transitioning from a WORKSTATION-based to a DOMAIN-based environment represents a significant shift towards improved productivity and manageability of network resources. Implementing Role-Based Access Control (RBAC) is a key aspect of this transition, ensuring that access to systems and file shares aligns with each user’s job function, thereby safeguarding sensitive data and trade secrets.
RBAC in Action: Setting Up File Shares
File shares in a DOMAIN environment can be organized as follows:
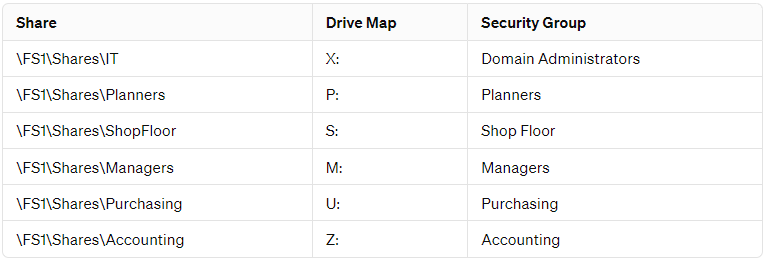
Permissions can be tailored within these shares, offering different levels of access to various groups. For instance, purchasing group members might have read-only access, while managers have full privileges.
Streamlining Access with Group Policy and Drive Mappings

Group policy can facilitate drive mappings to Universal Naming Convention (UNC) paths, simplifying how users access their file shares. Accurate documentation of job functions is crucial for assigning correct permissions from the outset, preventing access issues, and enhancing security.
Steps for Effective RBAC Implementation
- Identify Management Staff: Determine departmental managers and the location of network shares.
- Create Security Groups: Establish groups based on job roles, as outlined in the table above.
- Create User Accounts: Assign users to the appropriate groups according to their job functions.
- Migrate Files: Move files from individual workstations/network shares to designated file shares.
- Copy User Profiles: Transfer workgroup profiles to domain profiles to maintain a familiar desktop environment.
- Disable Workstation Logins: Ensure that users access the network through their new domain profiles.
By adhering to this process, IT departments can proactively manage user access, minimizing downtime and ensuring that data remains secure and properly backed up.






