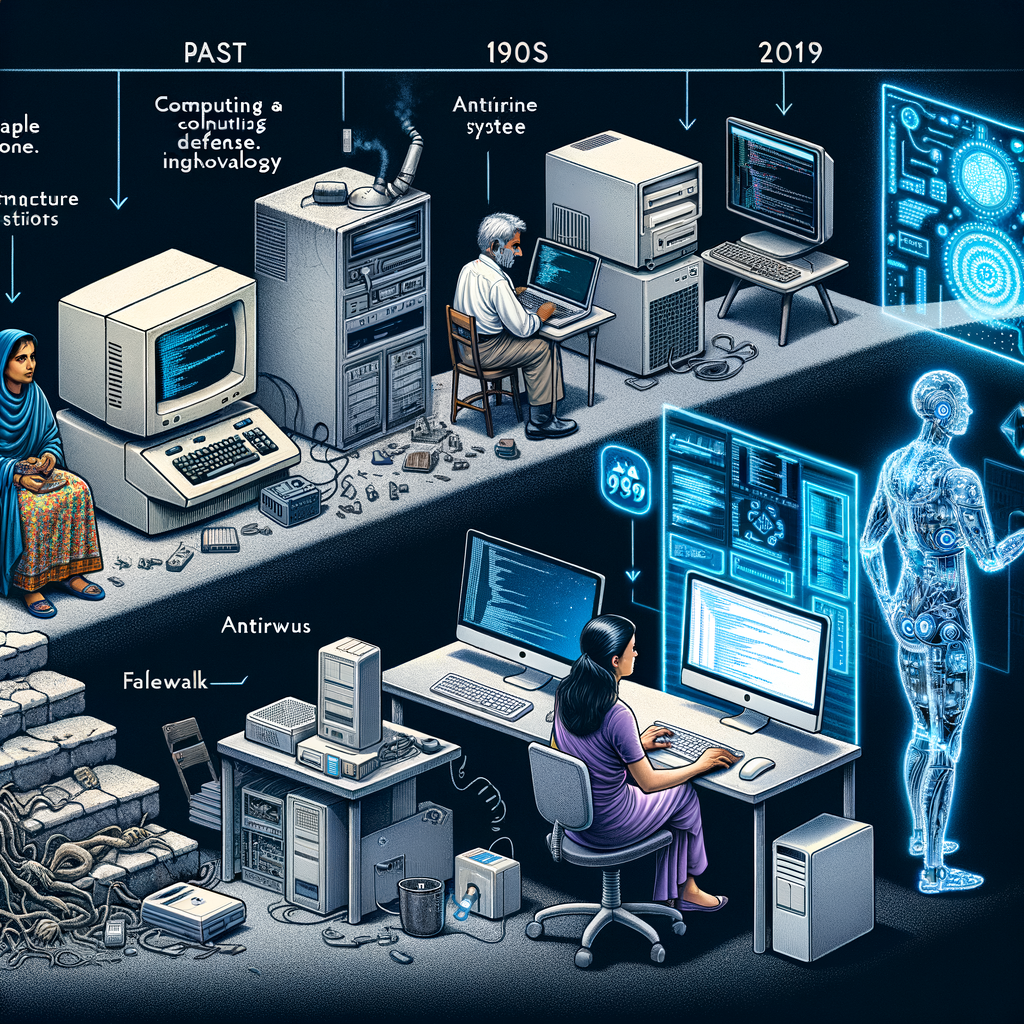
The evolution of cybersecurity is a complex journey that mirrors the advancement of technology and the ever-changing landscape of digital threats. From its rudimentary beginnings
The cybersecurity category offers a comprehensive exploration of digital security, focusing on topics like essential cybersecurity tips for small businesses, data backup methods, and digital privacy rights. It provides readers with in-depth knowledge and practical advice on safeguarding digital assets and navigating the complexities of the cybersecurity landscape.

The evolution of cybersecurity is a complex journey that mirrors the advancement of technology and the ever-changing landscape of digital threats. From its rudimentary beginnings

Ensuring data privacy in the cloud involves adopting a comprehensive approach that encompasses both technical measures and adherence to regulatory standards. As organizations increasingly migrate

In today’s digital landscape, small businesses have become a prime target for cyberattacks. As technology continues to advance, so do the tactics employed by malicious

In the realm of data protection, the debate between cloud and legacy backup methods remains pertinent. As businesses generate vast amounts of data, choosing the

In the digital age, investigative efforts often require extracting evidence from an individual’s online activities. One critical avenue is through Internet Service Providers (ISPs). They

In the realm of cybersecurity, understanding and integrating digital forensics into incident response is not just beneficial; it’s essential for comprehensive security management. They go

Voice Over IP (VoIP) technology, while revolutionizing the way we communicate, carries its own set of security challenges. VoIP, akin to any IP-based service, is

Digital Privacy and the Fourth Amendment: Navigating Modern Challenges In today’s digital age, the concept of digital privacy and our Fourth Amendment rights has evolved

In the realm of digital forensics and cybersecurity, Network Traffic Analysis Tools play a pivotal role in unraveling the complexities of network activities. These tools

Mobile Forensics: A Comprehensive Guide Mobile forensics is an essential aspect of modern investigative processes. As mobile phones evolve, becoming more sophisticated and computer-like, the

In the realm of digital forensics, especially on Macintosh systems, the importance of reliable data recovery tools cannot be overstated. Whether files were lost accidentally

In the realm of digital forensics, understanding the nuances between Windows and Macintosh systems is crucial for conducting effective investigations. Despite both being popular operating